Govern Access,
Reduce Risk.
Govern Access,
Reduce Risk.
Opal is the identity governance control plane for AI agents, humans, and service accounts at hypergrowth enterprises.
Opal is the identity governance control plane for AI agents, humans, and service accounts at hypergrowth enterprises.
Opal is the identity governance control plane for AI agents, humans, and service accounts at hypergrowth enterprises.
Govern Access,
Reduce Risk.
Opal is the identity governance control plane for AI agents, humans, and service accounts at hypergrowth enterprises.
Search
Search
Search
Search
⌘+K
⌘+K
⌘+K
⌘+K
Catalog
Catalog
Catalog
Catalog
Requests
Requests
Requests
Requests
Access Reviews
Access Reviews
Access Reviews
Access Reviews
Admin
Admin
Admin
Admin
Risk Center
Risk Center
Risk Center
Risk Center
Inventory
Inventory
Inventory
Inventory
Events
Events
Events
Events
Dashboard
Dashboard
Dashboard
Dashboard
Explore
Explore
Explore
Explore
Configuration
Configuration
Configuration
Configuration
DS
DS
DS
DS
Daniel Stuart
Daniel Stuart
Daniel Stuart
Daniel Stuart
Poplar Communications
Poplar Communications
Poplar Communications
Poplar Communications
Risk Center
Risk Center
Risk Center
Risk Center
Permanent Access
Permanent Access
Permanent Access
Permanent Access
82k
82k
82k
82k
Grants
Grants
Grants
Grants
+0.98%
+0.98%
+0.98%
+0.98%
Unused Access
Unused Access
Unused Access
Unused Access
968
968
968
968
Grants
Grants
Grants
Grants
+70.42%
+70.42%
+70.42%
+70.42%
Outside Access
Outside Access
Outside Access
Outside Access
26k
26k
26k
26k
Grants
Grants
Grants
Grants
+2.75%
+2.75%
+2.75%
+2.75%
Irregular Access
Irregular Access
Irregular Access
Irregular Access
568
568
568
568
Grants
Grants
Grants
Grants
+68.05%
+68.05%
+68.05%
+68.05%
Suggestions
Suggestions
Suggestions
Suggestions
View access from overprovisioned rules
View access from overprovisioned rules
View access from overprovisioned rules
View access from overprovisioned rules
poplar-project-002
poplar-project-002
poplar-project-002
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
View potentially anomalous access grants
View potentially anomalous access grants
View potentially anomalous access grants
Administrat
Administrat
Administrat
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Access Risk Summary
Access Risk Summary
Access Risk Summary
Today
Today
Today
Today
This Week
This Week
This Week
This Week
This Month
This Month
This Month
This Month
Total
Total
Total
Total
By Identity Type
By Identity Type
By Identity Type
By Identity Type
184 Access Grants
184 Access Grants
184 Access Grants
184 Access Grants
Identity
Identity
Identity
Identity
Asset
Asset
Asset
Asset
Expiration
Expiration
Expiration
Expiration
First Granted
First Granted
First Granted
First Granted
Last Used
Last Used
Last Used
Last Used
Vulnerabilities
Vulnerabilities
Vulnerabilities
Vulnerabilities
ZN
ZN
ZN
ZN
Zuri Nichols
Zuri Nichols
Zuri Nichols
Zuri Nichols
zuri@poplarcomm.net
zuri@poplarcomm.net
zuri@poplarcomm.net
zuri@poplarcomm.net
Teams Administrator
Teams Administrator
Teams Administrator
Teams Administrator
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Permanent
Permanent
Permanent
Permanent
15 days ago
15 days ago
15 days ago
15 days ago
Not available
Not available
Not available
Not available
Expire in 7 days
Expire in 7 days
Expire in 7 days
Expire in 7 days
DP
DP
DP
DP
Denise Pratt
Denise Pratt
Denise Pratt
Denise Pratt
denise@poplarcomm.net
denise@poplarcomm.net
denise@poplarcomm.net
denise@poplarcomm.net
Billing Administrator
Billing Administrator
Billing Administrator
Billing Administrator
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Permanent
Permanent
Permanent
Permanent
15 days ago
15 days ago
15 days ago
15 days ago
Not available
Not available
Not available
Not available
Expire in 7 days
Expire in 7 days
Expire in 7 days
Expire in 7 days
RP
RP
RP
RP
Rita Patel
Rita Patel
Rita Patel
Rita Patel
rita@poplarcomm.net
rita@poplarcomm.net
rita@poplarcomm.net
rita@poplarcomm.net
Finance Team Admin
Finance Team Admin
Finance Team Admin
Finance Team Admin
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Permanent
Permanent
Permanent
Permanent
15 days ago
15 days ago
15 days ago
15 days ago
Not available
Not available
Not available
Not available
Expire in 7 days
Expire in 7 days
Expire in 7 days
Expire in 7 days
ZN
ZN
ZN
ZN
Zuri Nichols
Zuri Nichols
Zuri Nichols
Zuri Nichols
zuri@poplarcomm.net
zuri@poplarcomm.net
zuri@poplarcomm.net
zuri@poplarcomm.net
Teams Administrator
Teams Administrator
Teams Administrator
Teams Administrator
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Azure • Entra ID Role
Permanent
Permanent
Permanent
Permanent
15 days ago
15 days ago
15 days ago
15 days ago
Not available
Not available
Not available
Not available
Expire in 7 days
Expire in 7 days
Expire in 7 days
Expire in 7 days
Ask Opal
Summary
Recommendation: Revoke permanent access for Teams Administrator for Zuri Nichols and implement just-in-time access instead.
Justification
Zuri Nichols currently has permanent access to Teams Administrator, which is classified as a medium sensitivity asset. Two significant risk factors have been identified:
Permanent access: Maintaining permanent access to administrative systems violates the principle of least privilege and creates unnecessary standing access risk.
Externally granted access: The access was granted outside of standard access management workflows, indicating potential governance gaps and lack of proper approval processes.
Teams Administrator privileges can be particularly risky as they allow for managing team memberships, communication settings, and potentially sensitive collaboration spaces. Following security best practices, administrative access should be:
Do Nothing
Expire in 7 days
Expire Now
Search
⌘+K
Catalog
Requests
Access Reviews
Admin
Risk Center
Inventory
Events
Dashboard
Explore
Configuration
DS
Daniel Stuart
Poplar Communications
Risk Center
Permanent Access
82k
Grants
+0.98%
Unused Access
968
Grants
+70.42%
Outside Access
26k
Grants
+2.75%
Irregular Access
568
Grants
+68.05%
Suggestions
View access from overprovisioned rules
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Today
This Week
This Month
Total
By Identity Type
184 Access Grants
Identity
Asset
Expiration
First Granted
Last Used
Vulnerabilities
ZN
Zuri Nichols
zuri@poplarcomm.net
Teams Administrator
Azure • Entra ID Role
Permanent
15 days ago
Not available
Expire in 7 days
DP
Denise Pratt
denise@poplarcomm.net
Billing Administrator
Azure • Entra ID Role
Permanent
15 days ago
Not available
Expire in 7 days
RP
Rita Patel
rita@poplarcomm.net
Finance Team Admin
Azure • Entra ID Role
Permanent
15 days ago
Not available
Expire in 7 days
ZN
Zuri Nichols
zuri@poplarcomm.net
Teams Administrator
Azure • Entra ID Role
Permanent
15 days ago
Not available
Expire in 7 days
Ask Opal
Summary
Recommendation: Revoke permanent access for Teams Administrator for Zuri Nichols and implement just-in-time access instead.
Justification
Zuri Nichols currently has permanent access to Teams Administrator, which is classified as a medium sensitivity asset. Two significant risk factors have been identified:
Permanent access: Maintaining permanent access to administrative systems violates the principle of least privilege and creates unnecessary standing access risk.
Externally granted access: The access was granted outside of standard access management workflows, indicating potential governance gaps and lack of proper approval processes.
Teams Administrator privileges can be particularly risky as they allow for managing team memberships, communication settings, and potentially sensitive collaboration spaces. Following security best practices, administrative access should be:
Do Nothing
Expire in 7 days
Expire Now
What we do
What we do
Secure AI adoption starts with identity governance.
Opal is the control layer that keeps access accurate, compliant, and contained.
Secure AI adoption starts with identity governance.
Opal is the control layer that keeps access accurate, compliant, and contained.
Secure AI adoption starts with identity governance.
Opal is the control layer that keeps access accurate, compliant, and contained.
Secure AI adoption starts with identity governance.
Opal is the control layer that keeps access accurate, compliant, and contained.
Identity Lifecycle Automation
Keep access current by orchestrating provisioning, updates, and removals in Opal or via Terraform.
Identity Lifecycle Automation
Keep access current by orchestrating provisioning, updates, and removals in Opal or via Terraform.
Identity Lifecycle Automation
Keep access current by orchestrating provisioning, updates, and removals in Opal or via Terraform.
JIT & Self-Service Access
Reduce sprawl and let users request and receive approved, time-bound access from Opal or Slack.
JIT & Self-Service Access
Reduce sprawl and let users request and receive approved, time-bound access from Opal or Slack.
JIT & Self-Service Access
Reduce sprawl and let users request and receive approved, time-bound access from Opal or Slack.
Access Reviews & Compliance
Simplify certifications and audits by automating UARs, evidence collection, and policy checks.
Access Reviews & Compliance
Simplify certifications and audits by automating UARs, evidence collection, and policy checks.
Access Reviews & Compliance
Simplify certifications and audits by automating UARs, evidence collection, and policy checks.
Access Reviews & Compliance
Simplify certifications and audits by automating UARs, evidence collection, and policy checks.
Identity Risk Management
Continuously detect and remediate risky access with full visibility and least-privilege enforcement.
Identity Risk Management
Continuously detect and remediate risky access with full visibility and least-privilege enforcement.
Identity Risk Management
Continuously detect and remediate risky access with full visibility and least-privilege enforcement.
Permanent Access
82k
Grants
+0.98%
Unused Access
968
Grants
+70.42%
Outside Access
26k
Grants
+2.75%
Irregular Access
568
Grants
+68.05%
Suggestions
View access from overprovisioned rules
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Today
This Week
This Month
Total
By Identity Type
184 Access Grants
Identity
Asset
Expiration
First Granted
Last Used
Vulnerabilities
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
09-28-google-idp
Google Cloud • Service Account
Permanent
19 minutes ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
09-28-google-idp
Google Cloud • Service Account
Permanent
5 hours ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
aiplatform.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian36288
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
adrian-backupdr
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.storage
Google Cloud • Service Account
Permanent
a month ago
Never used
Expire in 7 days
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
adrian.dev-owner
Google Cloud • Organization
Permanent
a month ago
Never used
Expire in 7 days
Adrian Security Group
Azure • Microsoft Entra ID Security Group
Cognitive Services Contributor
Azure • Storage Container
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian-folder
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
resourcemanager
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
Risk Center
Admin
FN
Ask Opal
1 Access Grant Selected
Expire in 7 days (Recommended)
Permanent Access
82k
Grants
+0.98%
Unused Access
968
Grants
+70.42%
Outside Access
26k
Grants
+2.75%
Irregular Access
568
Grants
+68.05%
Suggestions
View access from overprovisioned rules
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Today
This Week
This Month
Total
By Identity Type
184 Access Grants
Identity
Asset
Expiration
First Granted
Last Used
Vulnerabilities
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
09-28-google-idp
Google Cloud • Service Account
Permanent
19 minutes ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
09-28-google-idp
Google Cloud • Service Account
Permanent
5 hours ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
aiplatform.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian36288
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
adrian-backupdr
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.storage
Google Cloud • Service Account
Permanent
a month ago
Never used
Expire in 7 days
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
adrian.dev-owner
Google Cloud • Organization
Permanent
a month ago
Never used
Expire in 7 days
Adrian Security Group
Azure • Microsoft Entra ID Security Group
Cognitive Services Contributor
Azure • Storage Container
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian-folder
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
resourcemanager
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
Risk Center
Admin
FN
Ask Opal
1 Access Grant Selected
Expire in 7 days (Recommended)
Permanent Access
82k
Grants
+0.98%
Unused Access
968
Grants
+70.42%
Outside Access
26k
Grants
+2.75%
Irregular Access
568
Grants
+68.05%
Suggestions
View access from overprovisioned rules
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Today
This Week
This Month
Total
By Identity Type
184 Access Grants
Identity
Asset
Expiration
First Granted
Last Used
Vulnerabilities
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
09-28-google-idp
Google Cloud • Service Account
Permanent
19 minutes ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
09-28-google-idp
Google Cloud • Service Account
Permanent
5 hours ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
aiplatform.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian36288
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
adrian-backupdr
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.storage
Google Cloud • Service Account
Permanent
a month ago
Never used
Expire in 7 days
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
adrian.dev-owner
Google Cloud • Organization
Permanent
a month ago
Never used
Expire in 7 days
Adrian Security Group
Azure • Microsoft Entra ID Security Group
Cognitive Services Contributor
Azure • Storage Container
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian-folder
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
resourcemanager
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
Risk Center
Admin
FN
Ask Opal
1 Access Grant Selected
Expire in 7 days (Recommended)
Permanent Access
82k
Grants
+0.98%
Unused Access
968
Grants
+70.42%
Outside Access
26k
Grants
+2.75%
Irregular Access
568
Grants
+68.05%
Suggestions
View access from overprovisioned rules
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Today
This Week
This Month
Total
By Identity Type
184 Access Grants
Identity
Asset
Expiration
First Granted
Last Used
Vulnerabilities
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
09-28-google-idp
Google Cloud • Service Account
Permanent
19 minutes ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
09-28-google-idp
Google Cloud • Service Account
Permanent
5 hours ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
aiplatform.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian36288
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
adrian-backupdr
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.storage
Google Cloud • Service Account
Permanent
a month ago
Never used
Expire in 7 days
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
adrian.dev-owner
Google Cloud • Organization
Permanent
a month ago
Never used
Expire in 7 days
Adrian Security Group
Azure • Microsoft Entra ID Security Group
Cognitive Services Contributor
Azure • Storage Container
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian-folder
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
resourcemanager
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
Risk Center
Admin
FN
Ask Opal
1 Access Grant Selected
Expire in 7 days (Recommended)
Permanent Access
82k
Grants
+0.98%
Unused Access
968
Grants
+70.42%
Outside Access
26k
Grants
+2.75%
Irregular Access
568
Grants
+68.05%
Suggestions
View access from overprovisioned rules
poplar-project-002
1 out of 2 users have permanent access and have not used this resource in the last 30 days.
View potentially anomalous access grants
Administrat
2 out of 3 users have permanent access and have not used this resource in the last 30 days.
Access Risk Summary
Today
This Week
This Month
Total
By Identity Type
184 Access Grants
Identity
Asset
Expiration
First Granted
Last Used
Vulnerabilities
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
09-28-google-idp
Google Cloud • Service Account
Permanent
19 minutes ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
09-28-google-idp
Google Cloud • Service Account
Permanent
5 hours ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
aiplatform.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.serviceagent
Google Cloud • Service Account
Permanent
4 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian36288
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
default service account
Google Cloud • Service Account
adrian-backupdr
Google Cloud • Service Account
Permanent
17 days ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
timbucket9.storage
Google Cloud • Service Account
Permanent
a month ago
Never used
Expire in 7 days
SM
Shrinjay Mukherjee
shrinjay@adriandev.net
adrian.dev-owner
Google Cloud • Organization
Permanent
a month ago
Never used
Expire in 7 days
Adrian Security Group
Azure • Microsoft Entra ID Security Group
Cognitive Services Contributor
Azure • Storage Container
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
adrian-folder
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
09-28-google-idp
Google Cloud • Service Account
resourcemanager
Google Cloud • Folder
Permanent
a month ago
Never used
Expire in 7 days
Risk Center
Admin
FN
Ask Opal
1 Access Grant Selected
Expire in 7 days (Recommended)
Built for every identity
Built for every identity
Opal governs every identity type under one model —
because security breaks and business slows when they’re managed apart.
Opal governs every identity type under one model —
because security breaks and business slows when they’re managed apart.
Opal governs every identity type under one model —
because security breaks and business slows when they’re managed apart.
How it works
The Opal Platform is a modern IGA control plane that unifies governance and security for every human and machine identity.
Discover
Orchestrate
Scale
Adapt
Autopilot
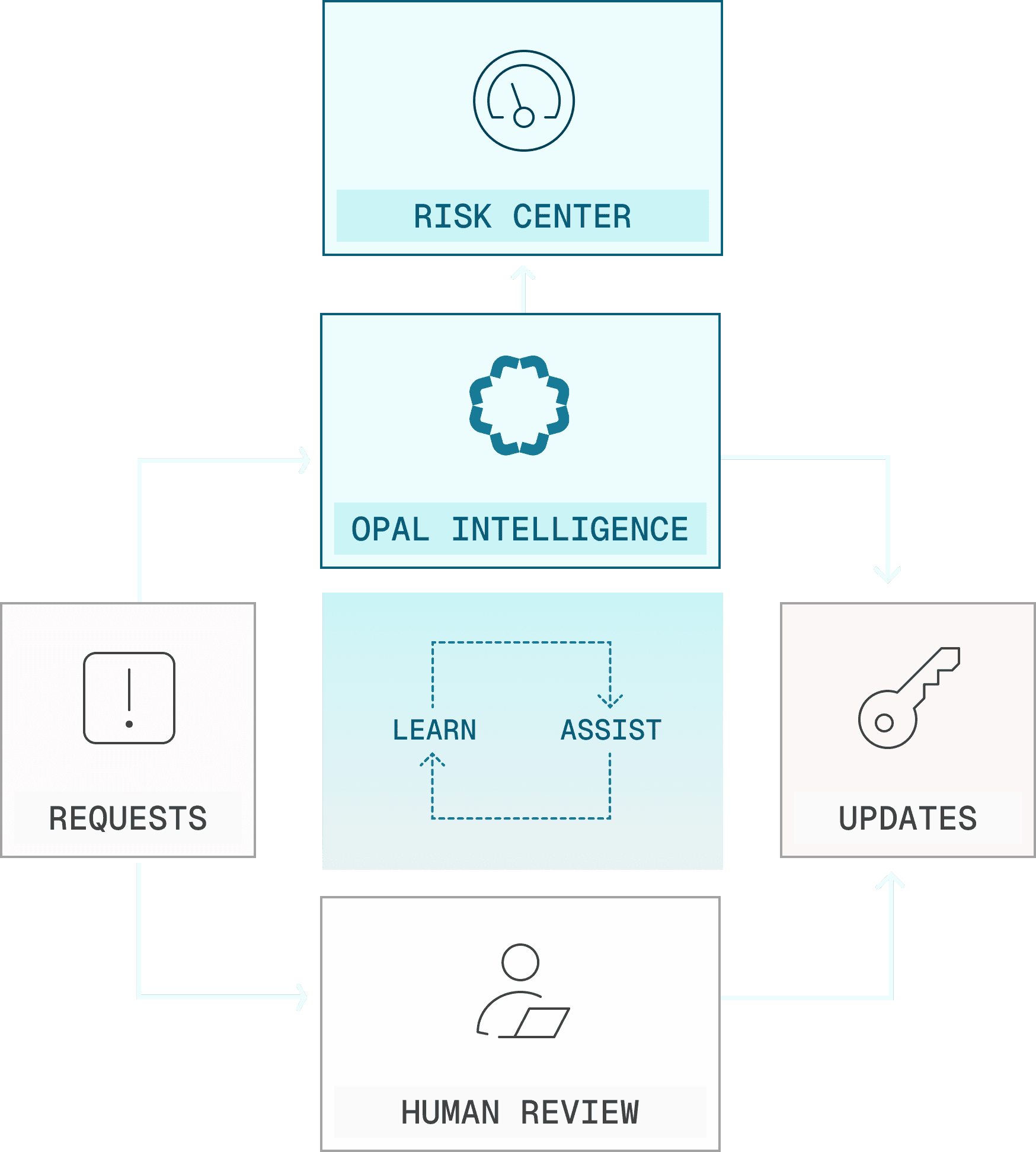
How it works
The Opal Platform is a modern IGA control plane that unifies governance and security for every human and machine identity.
Discover
Orchestrate
Scale
Adapt
Autopilot

FROM OUR Customers:
FROM OUR Customers:









