The Opal Platform
The Opal Platform
Continuous authorization, lifecycle management, and access governance for people, service accounts, and agents
Continuous authorization, lifecycle management, and access governance for people, service accounts, and agents
Continuous authorization, lifecycle management, and access governance for people, service accounts, and agents
Trusted by leading companies
Trusted by leading companies
Trusted by leading companies
Trusted by leading companies
How Opal empowers Security and IT to tackle authorization
How Opal empowers Security and IT to tackle authorization

Discover
See every identity. Understand every access path.
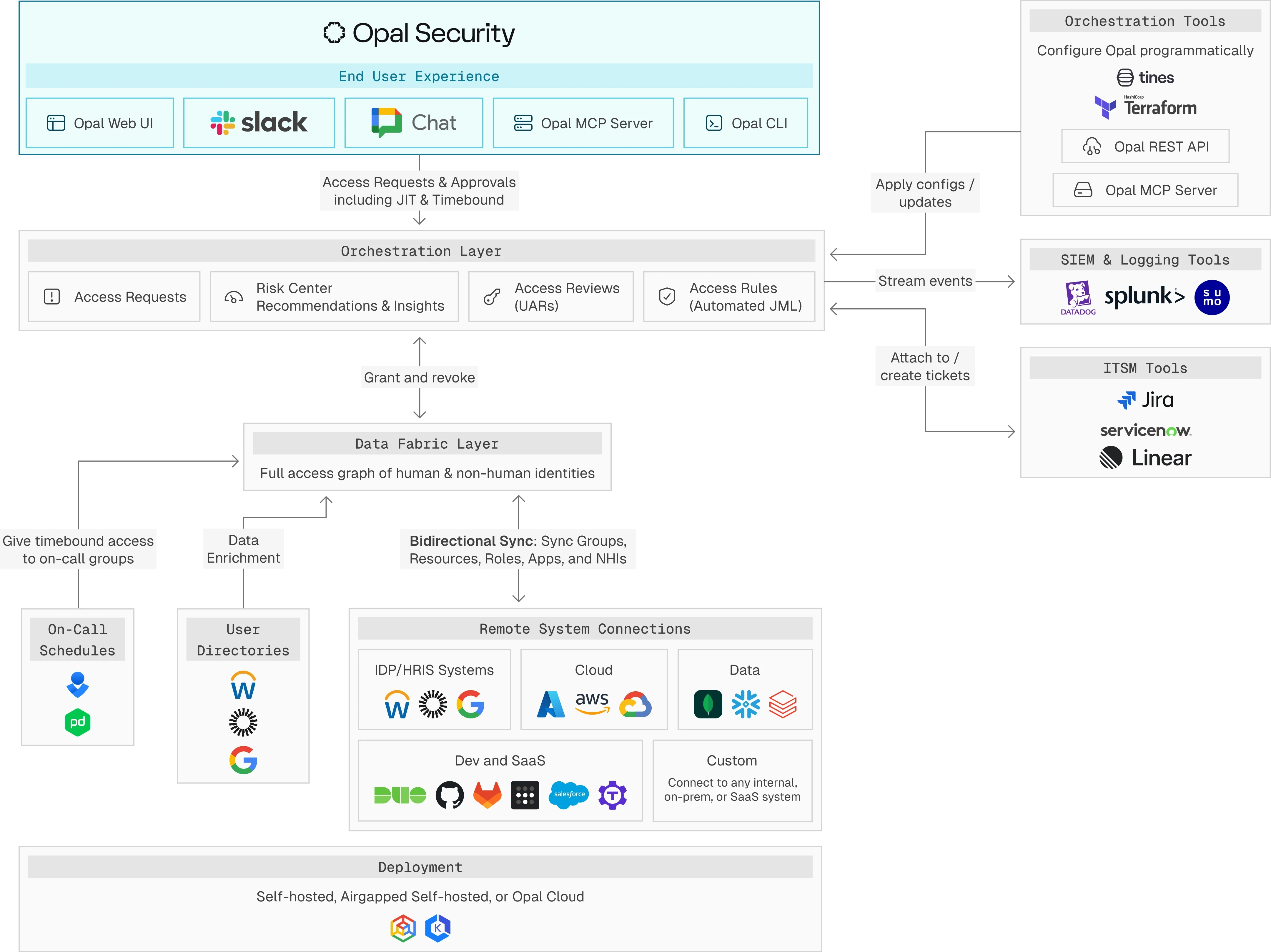
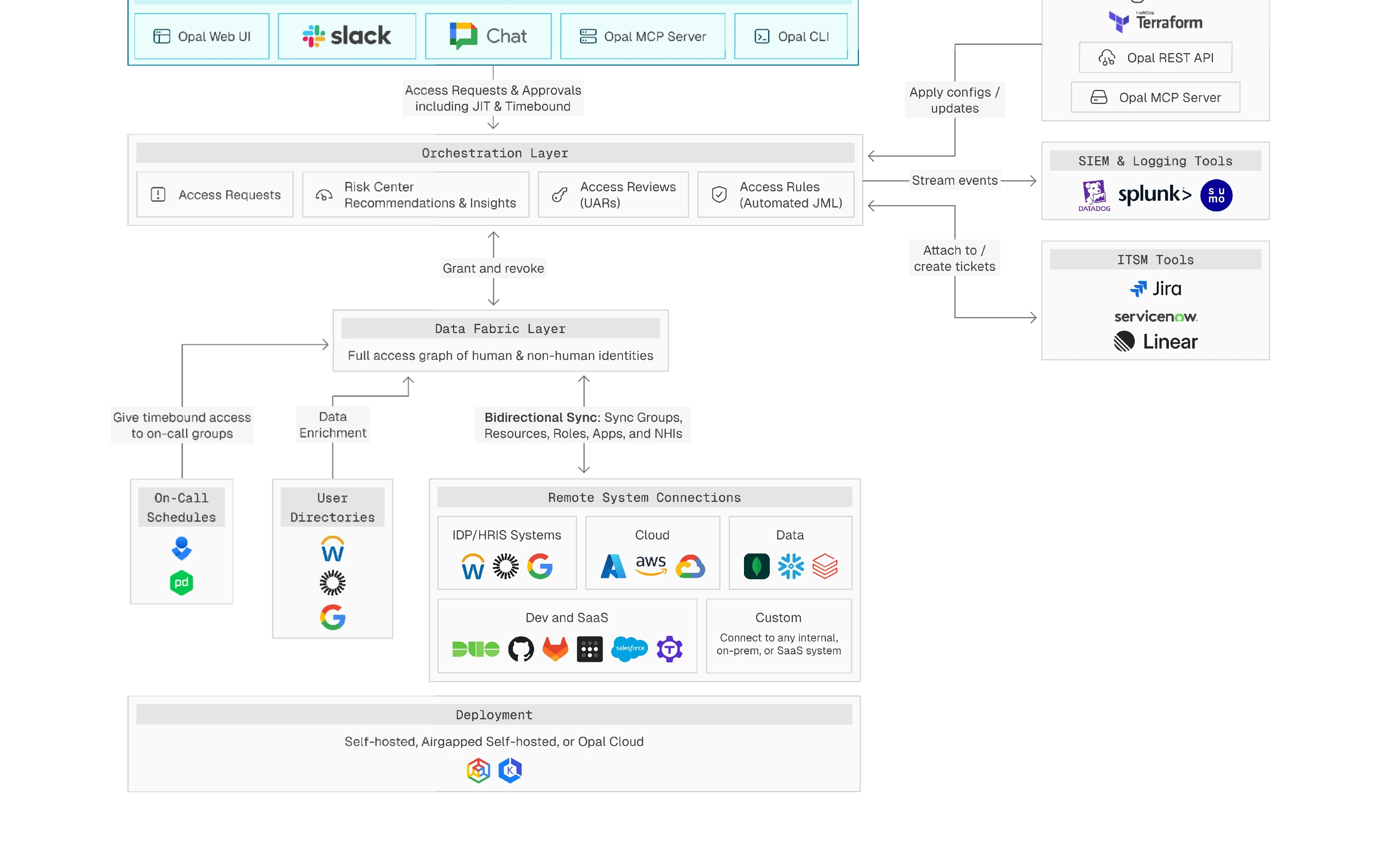
Opal integrates with your cloud and infrastructure to map human and machine identities in real time — giving security teams full visibility into who has access, where, and why.

Discover
See every identity. Understand every access path.
Opal integrates with your cloud and infrastructure to map human and machine identities in real time — giving security teams full visibility into who has access, where, and why.

Discover
See every identity. Understand every access path.
Opal integrates with your cloud and infrastructure to map human and machine identities in real time — giving security teams full visibility into who has access, where, and why.

Orchestrate
Shrink the attack surface — automatically.
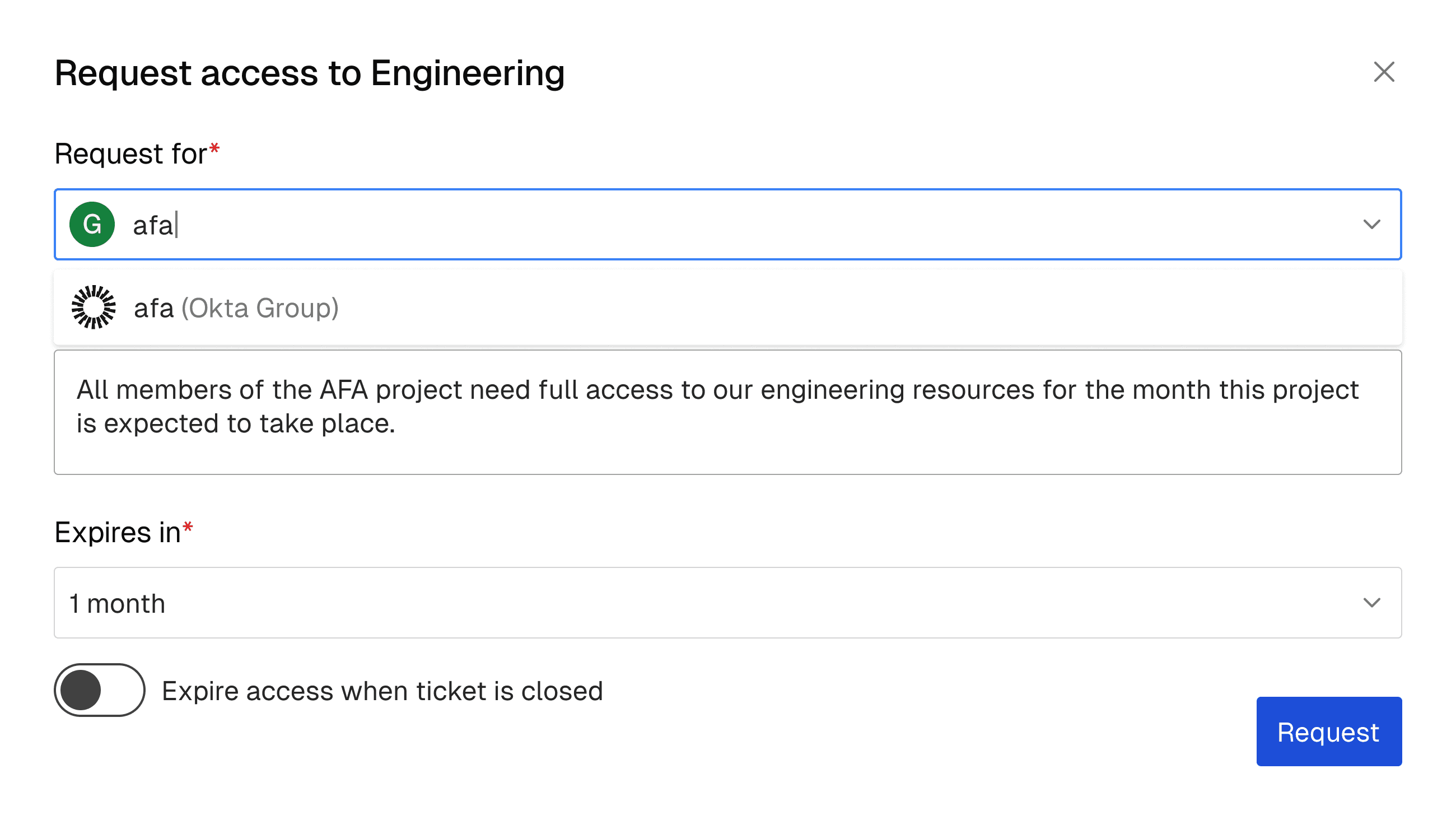
Opal enforces time-bound, JIT, and just-enough-access policies with native workflows that replace static roles, manual approvals, and out-of-band exceptions.
Orchestrate
Shrink the attack surface — automatically.
Opal enforces time-bound, JIT, and just-enough-access policies with native workflows that replace static roles, manual approvals, and out-of-band exceptions.

Orchestrate
Shrink the attack surface — automatically.
Opal enforces time-bound, JIT, and just-enough-access policies with native workflows that replace static roles, manual approvals, and out-of-band exceptions.

Orchestrate
Shrink the attack surface — automatically.
Opal enforces time-bound, JIT, and just-enough-access policies with native workflows that replace static roles, manual approvals, and out-of-band exceptions.

Orchestrate
Shrink the attack surface — automatically.
Opal enforces time-bound, JIT, and just-enough-access policies with native workflows that replace static roles, manual approvals, and out-of-band exceptions.

Scale
Extend control without adding friction.
Scale enforcement across SaaS, cloud, and internal systems with adaptable approval paths, delegated ownership, and breakglass logic built for fast-moving teams.

Scale
Extend control without adding friction.
Scale enforcement across SaaS, cloud, and internal systems with adaptable approval paths, delegated ownership, and breakglass logic built for fast-moving teams.

Scale
Extend control without adding friction.
Scale enforcement across SaaS, cloud, and internal systems with adaptable approval paths, delegated ownership, and breakglass logic built for fast-moving teams.

Adapt
Monitor for drift. Surface risk. Take action.
Opal continuously analyzes usage, behavior, and risk signals to flag toxic combinations, stale access, and privilege drift—then recommends what to fix, and when.

Adapt
Monitor for drift. Surface risk. Take action.
Opal continuously analyzes usage, behavior, and risk signals to flag toxic combinations, stale access, and privilege drift—then recommends what to fix, and when.

Adapt
Monitor for drift. Surface risk. Take action.
Opal continuously analyzes usage, behavior, and risk signals to flag toxic combinations, stale access, and privilege drift—then recommends what to fix, and when.

Autopilot
Keep access rightsized, hands-free.
Opal’s AI-driven remediation engine closes the loop — automating rightsizing, surfacing anomalies, and freeing up security teams to focus on strategy, not tickets.

Autopilot
Keep access rightsized, hands-free.
Opal’s AI-driven remediation engine closes the loop — automating rightsizing, surfacing anomalies, and freeing up security teams to focus on strategy, not tickets.

Autopilot
Keep access rightsized, hands-free.
Opal’s AI-driven remediation engine closes the loop — automating rightsizing, surfacing anomalies, and freeing up security teams to focus on strategy, not tickets.
How Opal Empowers Security Teams
How Opal Empowers Security Teams
Ownership
IT, Security, Engineering, and Compliance working together
Ownership
IT, Security, Engineering, and Compliance working together
Ownership
IT, Security, Engineering, and Compliance working together
Ownership
IT, Security, Engineering, and Compliance working together
Control
Granular, real time policy-based control and remediation
Control
Granular, real time policy-based control and remediation
Control
Granular, real time policy-based control and remediation
Control
Granular, real time policy-based control and remediation
Visibility
See and correlate access across humans and machines
Visibility
See and correlate access across humans and machines
Visibility
See and correlate access across humans and machines
Visibility
See and correlate access across humans and machines
Resiliency
An autonomous system that learns from past events
Resiliency
An autonomous system that learns from past events
Resiliency
An autonomous system that learns from past events
Resiliency
An autonomous system that learns from past events
How Opal Works